How to spot scam solicitor emails
The Solicitors Regulation Authority (SRA) understands the importance of vigilance in relation to cyber crime and has highlighted some of the more important areas to be briefed about within a release by its Chief Executive Paul Philip called IT Security: Keeping information and money safe.
In our article, Conveyancing scam could cost you £1,000s we highlighted the risk of fraud relating to bank details, however we are seeing new techniques being used and this article is aimed at helping you spot and combat these evolving threats.
What are the risks of scam solicitor emails?
Risk | What is it? | How can you spot it? |
Virus | viruses can cause anything from comparatively minor to very serious damage to your hardware, software or files. You can only get a virus if a computer user runs an infected program from a link in an email or an attachment. If a solicitor gets a virus then the virus can spread to other computers both in their office and to their clients and other solicitors by sharing infecting files or sending e-mails with viruses as attachments in the e-mail. | The only way a virus can get into your PC is by clicking a link on an email, on a website or via a data stick or CD. Viruses need to be let in, they can't find their own way in. |
Worm | A worm is like a virus and spreads from computer to computer, but unlike a virus, it has the capability to travel without any help from a person. A worm is very dangerous for a conveyancing solicitor as it can copy itself and email your contact list. | The only way a worm can get into your PC is by clicking a link on an email, on a website or via a data stick or CD - just like a virus. |
Trojan | A Trojan horse is not a virus. It is a destructive program that mimics a genuine application - it might, for example, look like a link to a OneDrive file. Unlike viruses, Trojan horses do not replicate themselves but they can be just as destructive. Trojans also open a backdoor entry to your computer which gives malicious users and/or programs access to your system, allowing confidential and personal information to be stolen. | Aa Trojan can only gain access to your system if you let them like a virus or worm. |
4 Tips on how to spot and combat scam emails and email hacking
- 1
Check the download link from clients
- 2
Check the name and email address
Scam email addresses and names to watch out for:
Name of Sender | Scam email address of sender |
Robert Arthur | simbeta@outlook.com - now not all emails like this are scam as many clients use an alias such as pinkfloyd@gmail.com or cheesegrater1978@yahoo.co.uk however you will need to clarify with your client that this is a real email and not a scam. |
Rachelle Moskowitz | Kingford Solicitors | kingsfordsolicitors@usfirstitle.com - if this was from Kingford Solicitors then the domain for the email wouldn't state @usfirstitle.com. |
James Woods | Savills | james.woods@saviills.co.uk - if this was from Savills then the domain for the email would be Savills not using two ii's - saviills |
- 3
Were you expecting the email?
- Microsoft Outlook - Your account has been temporarily blocked. Click the link to activate.
- Microsoft Outlook - Message failure.
- Microsoft Onedrive - Click to download documents.
Here are some examples of what scam emails look like
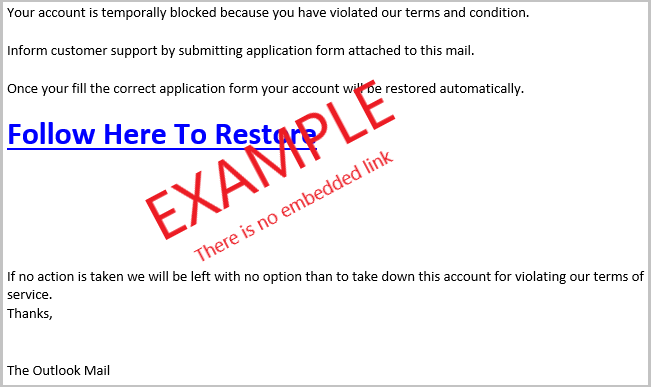
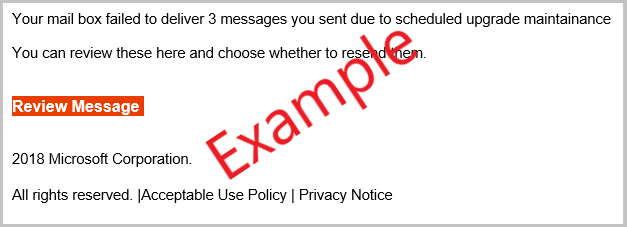
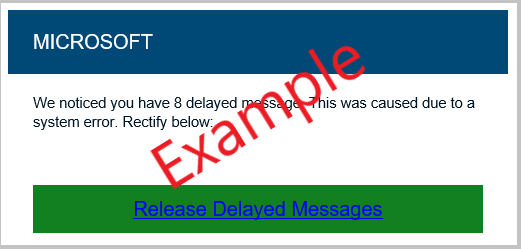
- 4
Some emails look very real
- Email format - does the email have a salutation, use first names (or last if this is your normal communication style) and does the signature look the same as previous emails received? Scammers struggle to replicate the formal format of a solicitor.
- Does the email make sense? - scammers aren't property solicitors so the context in the email is often incorrect.
- Spelling and grammar - as sophisticated as email hackers are, their spelling and grammar are more often than not atrocious. Look for this as a sign of a scam email (see the example email below).
- Are the email address and name the same? - unless the email hackers have access to your email exchange they are unable to email from your email account. For example, only our company can email from my email address (unless your computer has been hacked - see below) andrew@samconveyancing.co.uk. However, email scammers often use similar email addresses to make it seem the email address is correct. For example, andrew@ssamconveyancing.post or andrewsamconveyancing@post.com. The SRA reported in 2017 that 500 law firms had been targeted by clients using this approach (these are just the reported cases).
Example of scam email content
What can you do to protect yourself?
What can you do if you have been hacked?
How do you report cyber fraud and scams to the SRA?
Andrew started his career in 2000 working within conveyancing solicitor firms and grew hands-on knowledge of a wide variety of conveyancing challenges and solutions. After helping in excess of 50,000 clients in his career, he uses all this experience within his article writing for SAM, mainstream media and his self published book How to Buy a House Without Killing Anyone.
Caragh is an excellent writer and copy editor of books, news articles and editorials. She has written extensively for SAM for a variety of conveyancing, survey, property law and mortgage-related articles.








